DRAPASEC™ Vulnerability Management & Penetration Testing

Penetration Testing
A Penetration Testing service involves simulating real-world cyberattacks on an organization’s systems, applications, and networks to identify and exploit vulnerabilities. This proactive approach helps uncover security weaknesses that could be exploited by malicious actors. Pen testers use a combination of automated tools and manual techniques to mimic the tactics of real attackers, providing a detailed report on vulnerabilities, exploited weaknesses, and potential impacts. The goal is to enhance the organization’s security posture by addressing identified issues before they can be exploited in a real attack.
Get in touchCloud Penetration Testing
A Cloud Penetration Testing service involves simulating cyberattacks on an organization’s cloud-based infrastructure and applications to identify vulnerabilities and security weaknesses. This specialized form of penetration testing focuses on cloud environments, including services like AWS, Azure, and Google Cloud Platform. The goal is to uncover potential security flaws that could be exploited by attackers, such as misconfigurations, inadequate access controls, and exposed sensitive data. By conducting cloud pentesting, organizations can proactively address these issues, ensuring their cloud assets are secure and compliant with industry standards.
Get in touch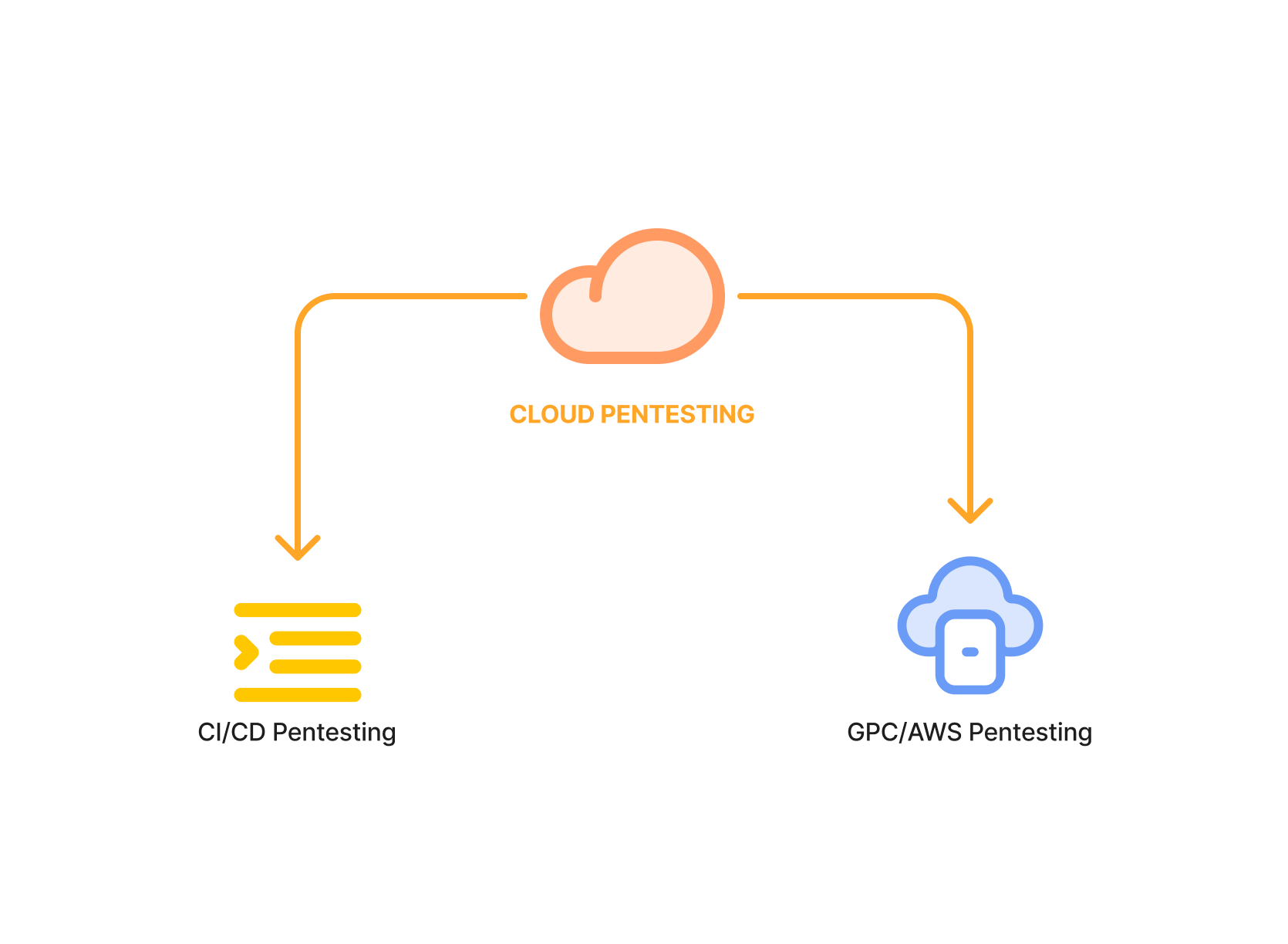
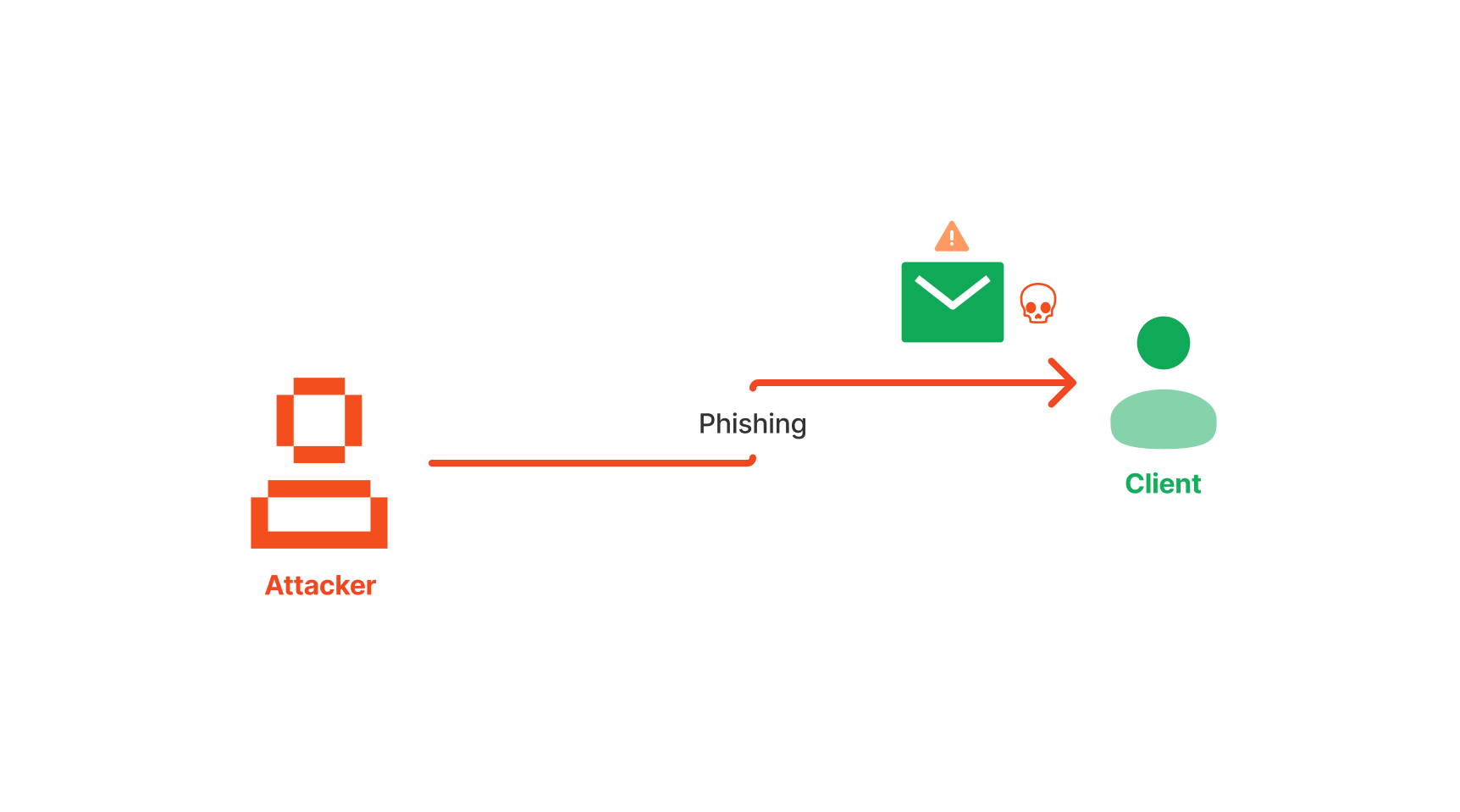
Social Engineering
A Social Engineering service involves simulating attacks that exploit human psychology to gain unauthorized access to sensitive information or systems. These attacks often involve tactics like phishing, pretexting, baiting, and tailgating to manipulate individuals into divulging confidential data or performing actions that compromise security. The goal is to identify vulnerabilities in human behavior and organizational processes, providing insights and recommendations to strengthen defenses against such manipulative tactics. By conducting social engineering assessments, organizations can enhance their security awareness and training programs, reducing the risk of successful social engineering attacks.
Get in touchRed Team Assessments
A Red Team Assessment is an advanced, simulated cyber-attack designed to test an organization’s security defenses by mimicking real-world threat actors’ tactics, techniques, and procedures (TTPs). This comprehensive evaluation involves a holistic view of the organization’s security posture, targeting technical, physical, and human vulnerabilities. The goal is to identify weaknesses that traditional penetration tests might miss, providing actionable insights to enhance security measures. By conducting a Red Team Assessment, organizations can better understand their ability to detect, respond to, and recover from sophisticated cyber-attacks, ultimately strengthening their overall security resilience
Get in touch

Purple Teaming Assessments
A Purple Team Assessment is a collaborative security exercise that combines the strengths of both Red Team (attackers) and Blue Team (defenders) to enhance an organization’s overall security posture. During this assessment, Red Team members simulate real-world attack scenarios, while Blue Team members work to detect, respond to, and mitigate these attacks in real-time. The goal is to improve communication and collaboration between offensive and defensive teams, identify gaps in security controls, and enhance the organization’s ability to detect and respond to threats. By conducting Purple Team Assessments, organizations can continuously refine their security strategies and ensure a more resilient defense against cyber threats
Get in touchActive Directory Security Assessments
An Active Directory Security Assessment is a comprehensive evaluation of the security posture of an organization’s Active Directory (AD) environment. This assessment focuses on identifying vulnerabilities, misconfigurations, and potential security risks within AD. It includes a review of operational processes, privileged account management, domain and forest configurations, and compliance with security best practices. The goal is to provide actionable recommendations to enhance the security of the AD infrastructure, ensuring robust protection against unauthorized access and potential breaches.
Get in touch

Application Vulnerability Scan
An Application Vulnerability Scan is an automated process that identifies security weaknesses in web applications. This scan checks for common vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure configurations. By using specialized tools, the scan simulates attacks to uncover potential security flaws that could be exploited by malicious actors. The goal is to provide a detailed report of identified vulnerabilities, along with recommendations for remediation. Regular application vulnerability scans help organizations maintain a strong security posture and protect their applications from evolving threats.
Get in touchIoT Security Assessments
An IoT Security Assessment is a comprehensive evaluation of the security posture of Internet of Things (IoT) devices and ecosystems. This assessment focuses on identifying vulnerabilities, misconfigurations, and potential threats specific to IoT environments. It includes a thorough review of IoT architecture, device security, firmware analysis, and connected interfaces. The goal is to ensure robust security controls are in place to protect against unauthorized access, data breaches, and other cyber threats. By conducting IoT Security Assessments, organizations can safeguard their IoT deployments, ensuring compliance with industry standards and enhancing overall security resilience.
Get in touch
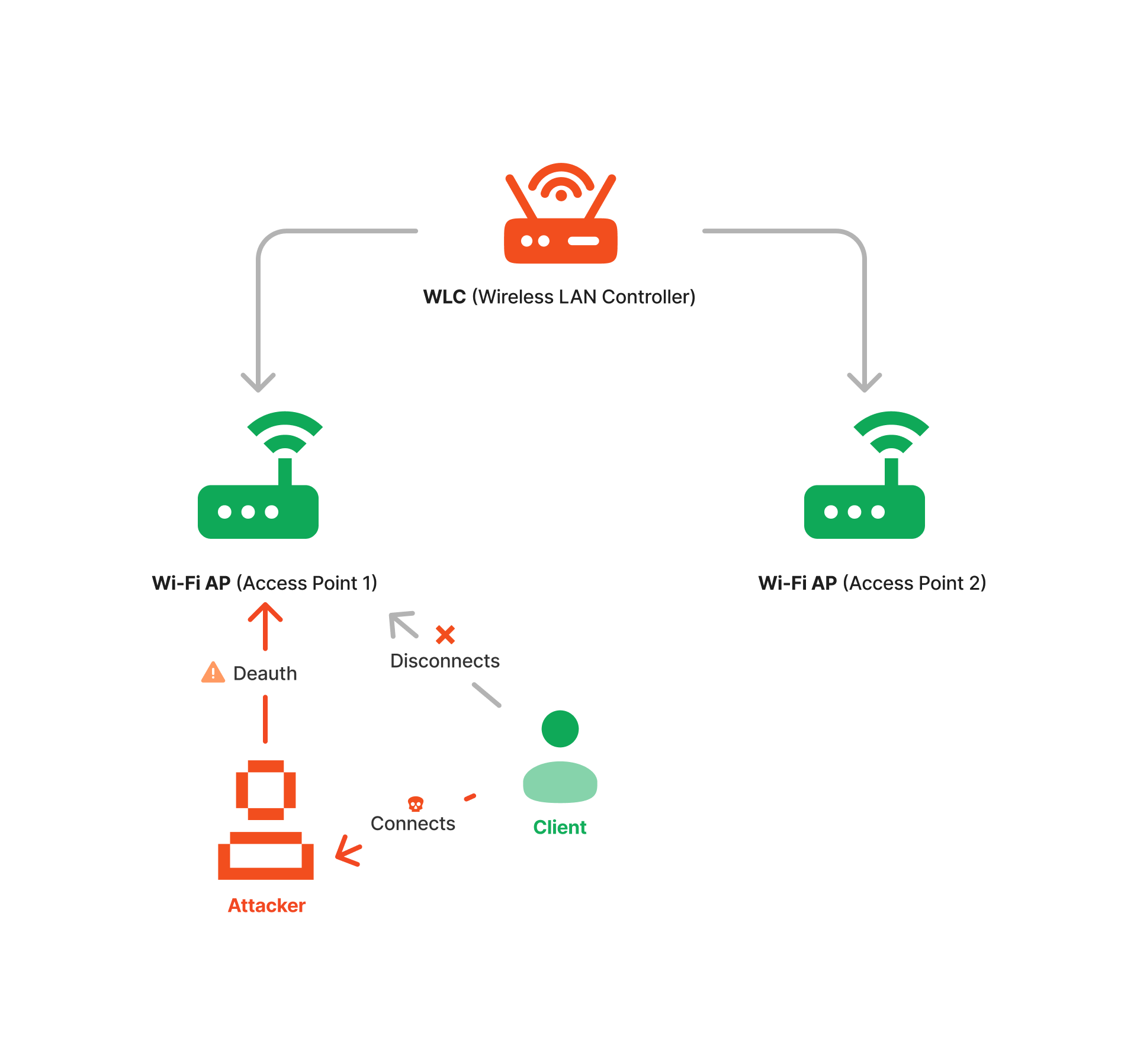
Wireless Assessments
A Wireless Penetration Testing service involves evaluating the security of an organization’s wireless networks by simulating attacks to identify vulnerabilities. This assessment focuses on uncovering weaknesses in Wi-Fi configurations, encryption protocols, and access controls. Pen testers use various techniques to exploit these vulnerabilities, such as unauthorized access, data interception, and denial of service attacks. The goal is to provide a detailed report of identified security gaps and recommend measures to strengthen the wireless network’s defenses. By conducting wireless pentesting, organizations can ensure their wireless infrastructure is secure against potential cyber threats.
Get in touch