DRAPASEC™ Application Security
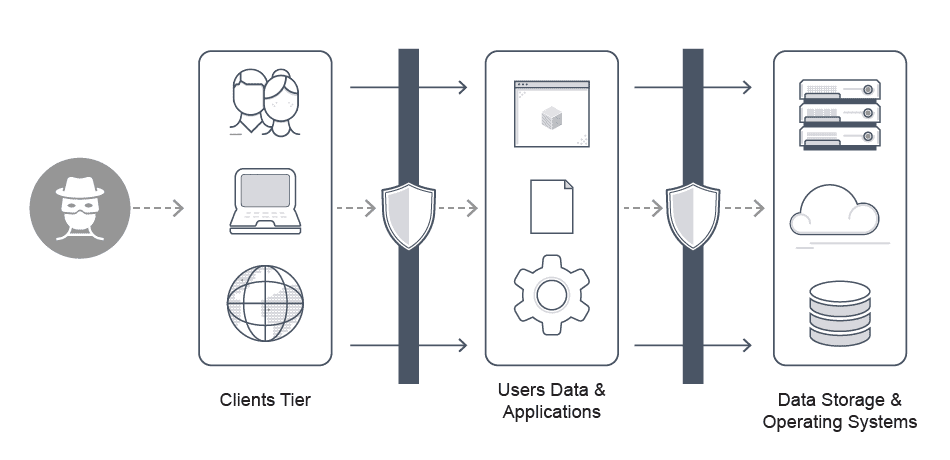

Application Security Architecture Review
An Application Security Architecture Assessment is a comprehensive evaluation of an application’s design and architecture to identify potential security vulnerabilities and weaknesses.
Here are some key aspects:
- Threat Modeling: Identifying potential threats and attack vectors that could exploit vulnerabilities in the application.
- Security Controls Review: Evaluating the effectiveness of existing security controls, such as authentication, authorization, encryption, and logging mechanisms.
- Architecture Analysis: Examining the application’s architecture to ensure it follows security best practices and industry standards.
- Code Review: Analyzing the source code for security flaws and vulnerabilities that could be exploited by attackers.
- Compliance Check: Ensuring the application meets relevant regulatory and compliance requirements, such as GDPR, HIPAA, or PCI-DSS.
- Risk Assessment: Assessing the potential impact and likelihood of identified security risks, and prioritizing them for remediation.
Application Security Program Assessment
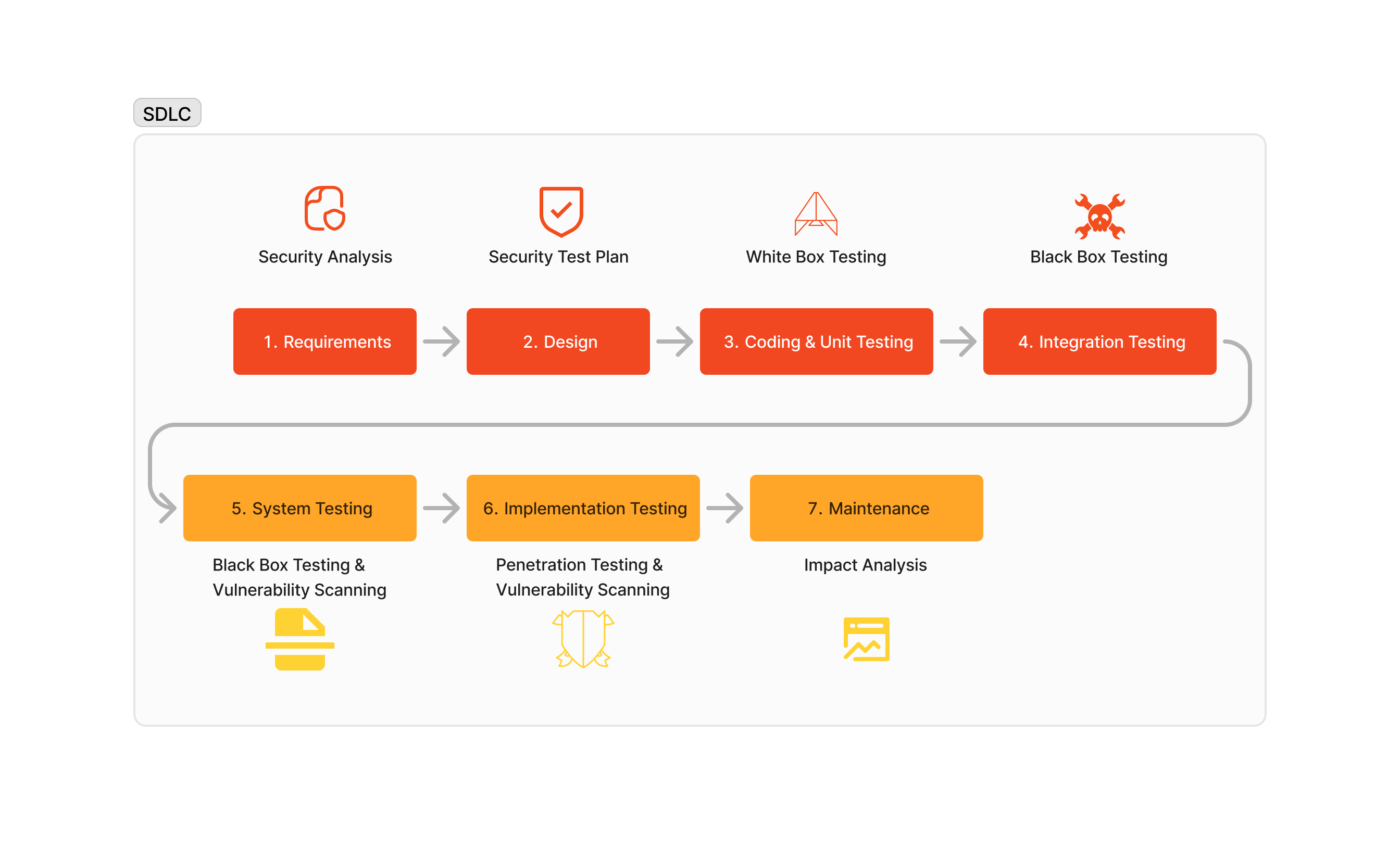
An Application Security Program Assessment is a comprehensive evaluation of an organization’s overall approach to securing its applications. Unlike a single application assessment, this program-level assessment looks at the broader security practices, policies, and controls in place across all applications within the organization.
Key components:
- Policy and Governance Review: Evaluating the organization’s security policies, standards, and governance structures to ensure they support robust application security.
- Risk Management: Assessing how the organization identifies, evaluates, and mitigates risks associated with its applications.
- Security Controls: Reviewing the effectiveness of security controls implemented across the application lifecycle, including development, testing, deployment, and maintenance.
- Compliance: Ensuring that the organization’s application security practices comply with relevant regulations and industry standards, such as OWASP SAMM or BSIMM1.
- Training and Awareness: Evaluating the effectiveness of security training programs for developers and other stakeholders to ensure they are aware of and can mitigate security risks.
- Incident Response: Assessing the organization’s ability to detect, respond to, and recover from security incidents affecting its applications.
- Continuous Improvement: Identifying areas for improvement and developing a roadmap to enhance the organization’s application security posture over time.
Application Threat Modeling
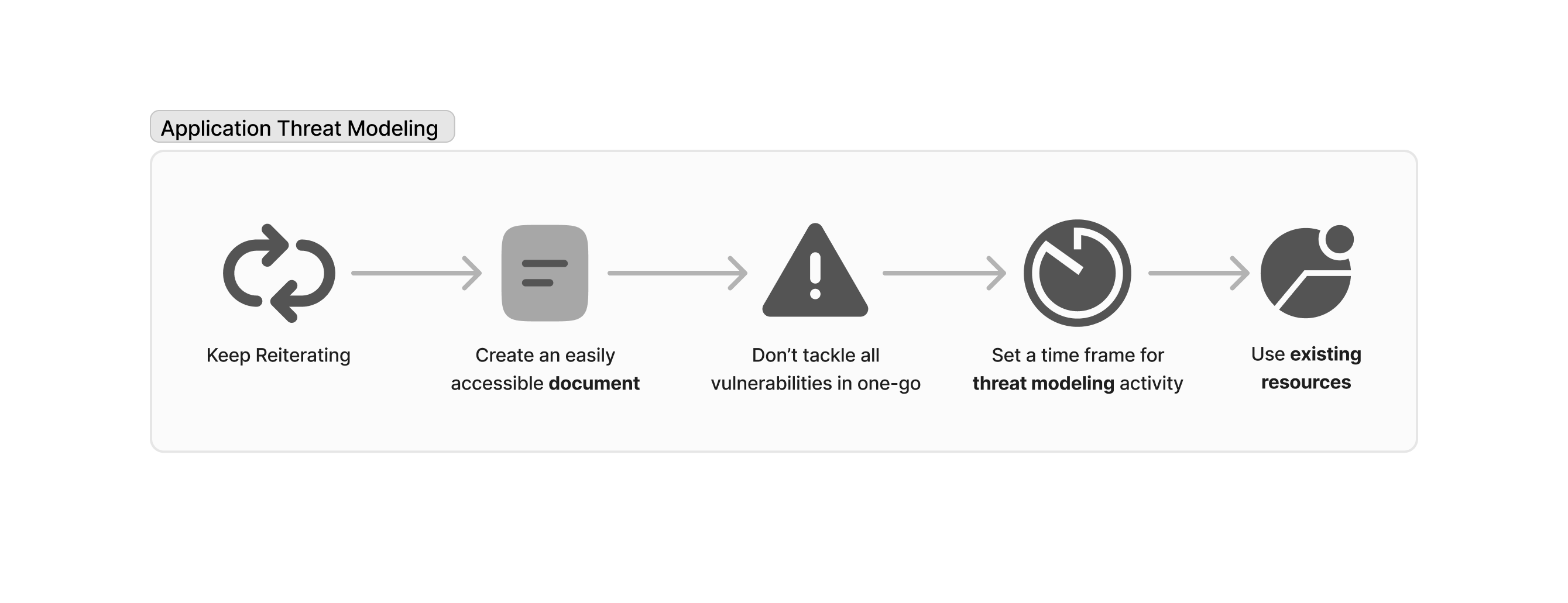
Application Threat Modeling is a structured process used to identify, analyze, and mitigate potential security threats and vulnerabilities within an application. Here’s a breakdown of what it involves:
- Identify Assets: Determine what valuable data or functionality needs protection within the application.
- Create an Architecture Overview: Develop a high-level diagram of the application’s architecture, including data flows, components, and interactions.
- Identify Threats: Use frameworks like STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) to systematically identify potential threats1.
- Identify Vulnerabilities: Look for weaknesses in the application that could be exploited by the identified threats.
- Determine Countermeasures: Develop strategies and controls to mitigate or eliminate the identified threats and vulnerabilities.
- Validate and Iterate: Continuously review and update the threat model as the application evolves and new threats emerge
Secure Software Development Training
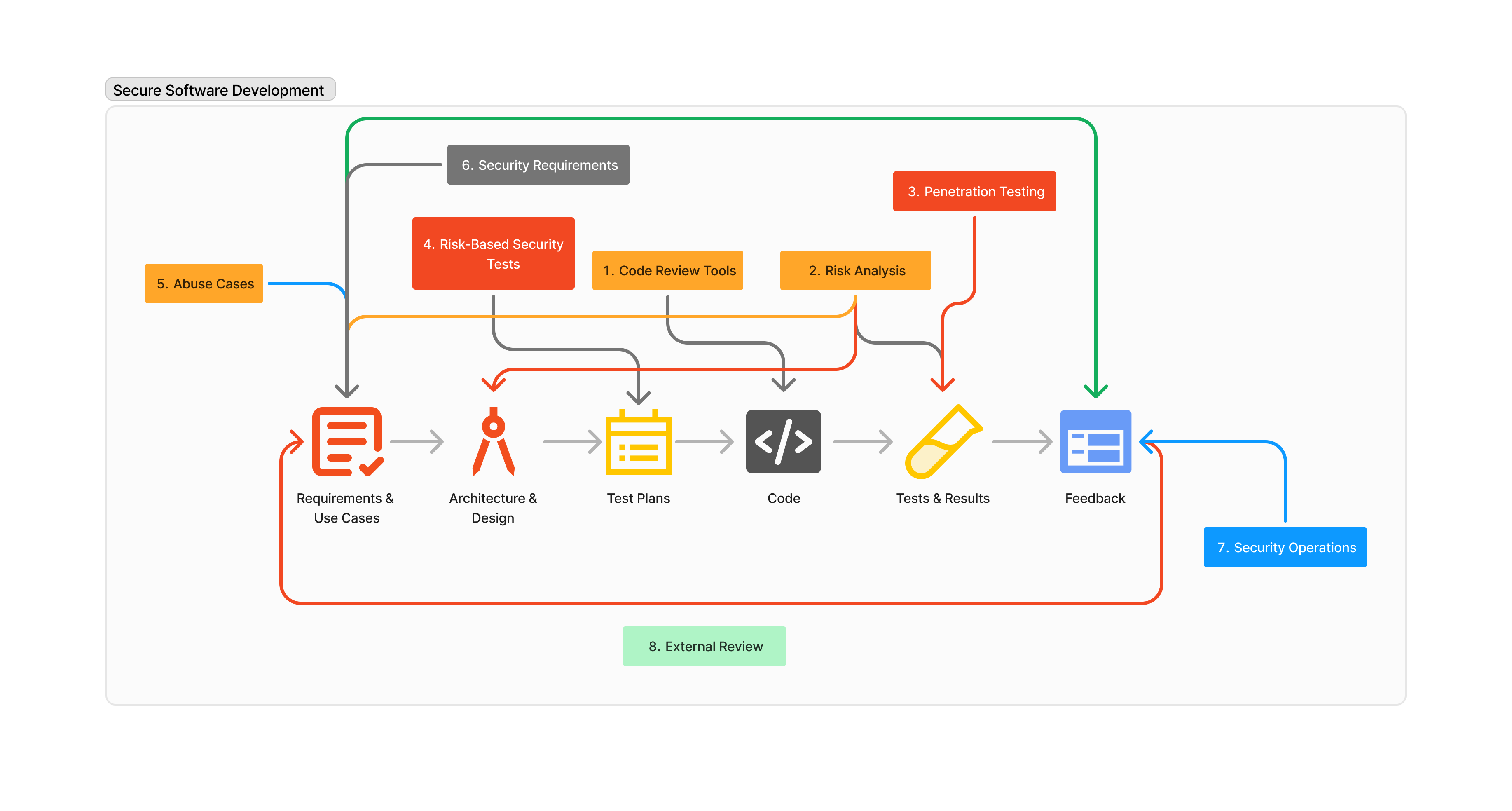
Secure Software Development Training:
Understanding Security Fundamentals: - Learn the basic principles of secure software development, including confidentiality, integrity, and availability.
- Familiarize yourself with common security threats and vulnerabilities, such as SQL injection, cross-site scripting (XSS), and buffer overflows.
Secure Coding Practices:
- Implement best practices for writing secure code, such as input validation, output encoding, and proper error handling.
- Use secure coding standards and guidelines to avoid introducing vulnerabilities.
Threat Modeling:
- Learn how to identify and assess potential threats to your application.
- Develop skills to create and use threat models to guide secure design and development.
Security Testing:
- Understand different types of security testing, including static and dynamic analysis, penetration testing, and code reviews.
- Learn how to use security testing tools to identify and fix vulnerabilities.
Secure Software Development Lifecycle (SDLC):
- Integrate security practices into each phase of the SDLC, from planning and design to implementation, testing, and maintenance.
- Learn how to create and maintain a secure development environment.
Compliance and Standards:
- Understand relevant security standards and regulations, such as OWASP, ISO/IEC 27001, and GDPR.
- Learn how to ensure your software meets these standards and complies with regulations.
Incident Response and Management:
- Develop skills to detect, respond to, and recover from security incidents.
- Learn how to create and implement an incident response plan.
Continuous Improvement:
- Stay updated with the latest security trends, threats, and best practices.
- Participate in ongoing training and professional development to enhance your security skills.
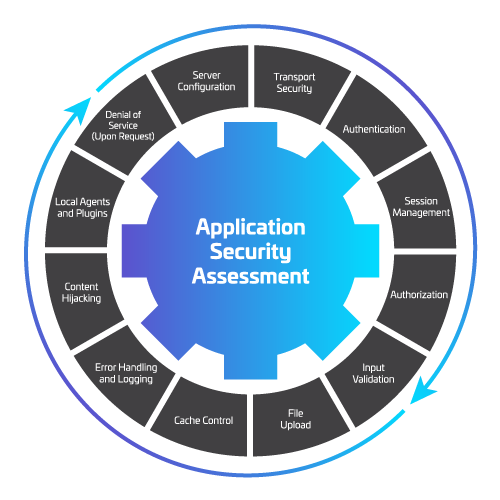
Application Security Assessment
An Application Security Assessment is a systematic evaluation of an application’s security posture. It involves identifying potential threats, vulnerabilities, and weaknesses within the application’s architecture, design, code, and infrastructure. The goal is to uncover security flaws that could be exploited by attackers and to recommend measures to mitigate these risks. This assessment helps organizations ensure their applications are secure, compliant with relevant regulations, and resilient against cyber threats.
Get in touchMobile App Security Assessment
A Mobile App Security Assessment is a thorough evaluation of a mobile application’s security posture. It aims to identify vulnerabilities, weaknesses, and potential threats specific to mobile environments. This assessment involves analyzing the app’s architecture, code, and configuration to uncover security flaws that could be exploited by attackers. The goal is to ensure the app is robust and resilient against security risks such as data breaches, unauthorized access, and code manipulation. By conducting regular mobile app security assessments, organizations can protect sensitive user data and maintain trust in their mobile applications.
Get in touch
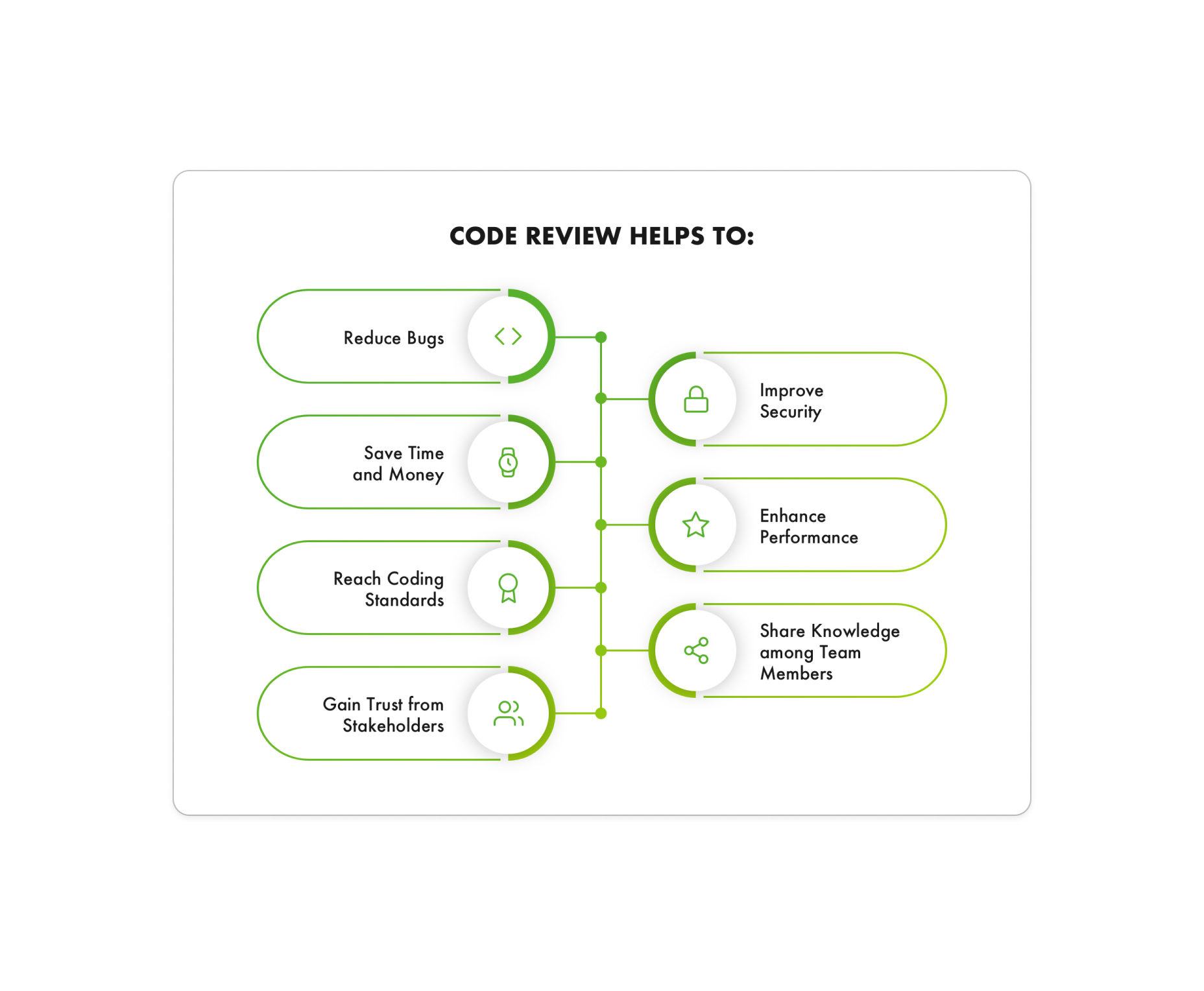
Source Code Review
A Source Code Review service involves a meticulous examination of an application’s source code to identify security vulnerabilities, coding errors, and potential performance issues. This process is crucial for ensuring the code’s integrity, security, and maintainability. Expert reviewers analyze the code line-by-line, using both automated tools and manual inspection to uncover hidden flaws that might not be detected through other testing methods. The goal is to enhance the overall quality of the code, prevent security breaches, and ensure compliance with industry standards. By leveraging a source code review service, organizations can deliver more secure and reliable software.
Get in touch